Microsoft had released an advisory stating the vulnerability in Internet Explorer 6, Internet Explorer 7, Internet Explorer 8, Internet Explorer 9, Internet Explorer 10, and Internet Explorer 11. Since the security fix is not available workarounds need to be applied to defend Internet Explorer vulnerability.
Workarounds that can be applied :
1) Disabling the ActiveX content by setting “High” Security Zone setting.
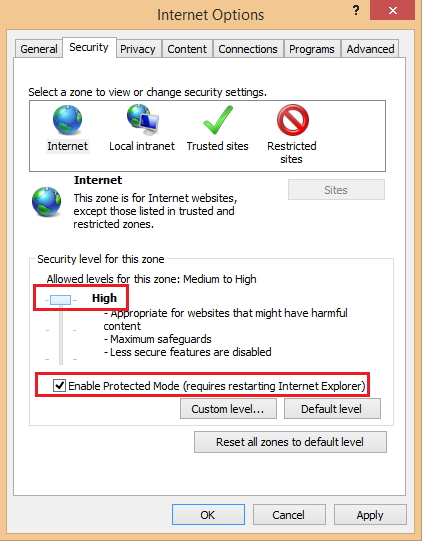
Perform the following steps to raise the Internet explorer’s security level :
- On the Internet Explorer Tools menu, click Internet Options.
- In the Internet Options dialog box, click the Security tab, and then click Internet.
- Under Security level for this zone, move the slider to High. This sets the security level for all websites you visit to High.
- Click Local intranet.
- Under Security level for this zone, move the slider to High. This sets the security level for all websites you visit to High.
- Click OK to accept the changes and return to Internet Explorer.
Note : This may change your browsing experience causing problems while browsing other websites too.
2) Enable Enhanced Protected Mode For Internet Explorer 11:
Internet Explorer 11 users can help protect against exploitation of this vulnerability by enabling Enhanced Protected Mode (EPM) settings in the browser. This security setting is available for Internet Explorer 11 on Windows 7 for x64-based systems, and all Windows 8 and Windows 8.1 systems.
Perform the following steps to enable EPM in Internet Explorer:
- On the Internet Explorer Tools menu, click Internet Options.
- In the Internet Options dialog box, click the Advanced tab, and then scroll down to the Security section of the settings list.
- Ensure the check boxes next to Enable Enhanced Protected Mode and Enable 64-bit processes for Enhanced Protected Mode (for 64-bit systems) are selected.
- Click OK to accept the changes and return to Internet Explorer.
- Restart your system.
3) Deploy the Microsoft Enhanced Mitigation Experience Toolkit 4.1:
The Enhanced Mitigation Experience Toolkit (EMET) helps mitigate or lessen the severity of the exploitation of this vulnerability.

This is done by adding additional protection layers like DEP, that makes the vulnerability harder to exploit.
4) Disable the Flash Plugin which helps in implementing the exploit. You can do so by following these steps:
- Open the Tools menu.
- Click Manage Add-Ons.
- Find the entry for Shockwave Flash Object and click it once. It will be highlighted in blue.
- Click the Disable button in the bottom right corner of the window.
- Restart your browser for changes to take affect.
5) The simplest yet most effective way would be to use another browser like Mozilla Firefox or Chrome till Microsoft release the security patch. This is a browser vulnerability and not a system so switching browser would defend against the Internet Explorer vulnerability.
The workarounds mentioned in this article will help you defend Internet Explorer Vulnerability.

Pingback: Microsoft Internet Explorer under Attack from Hackers | knotrick.com